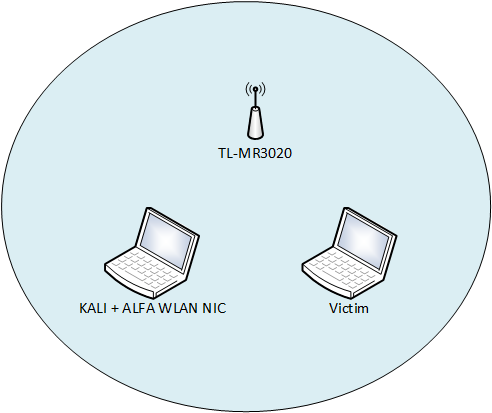
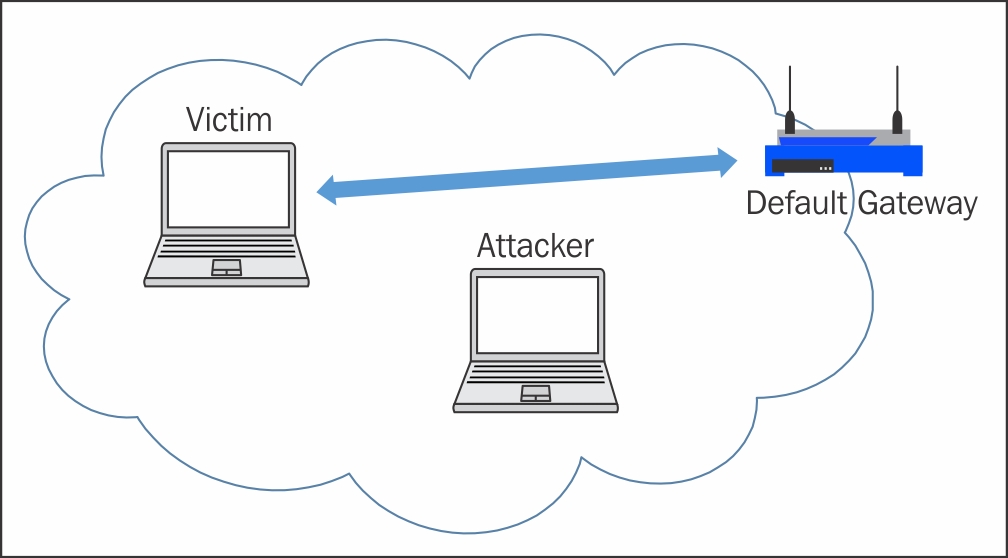
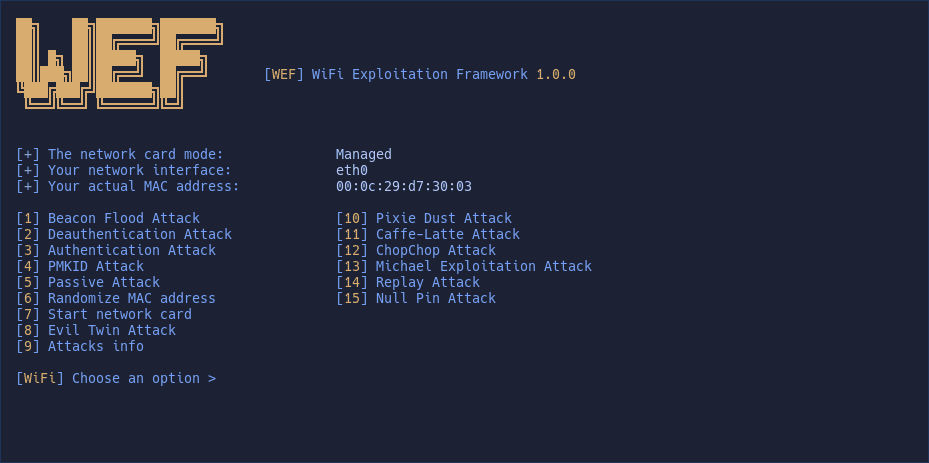
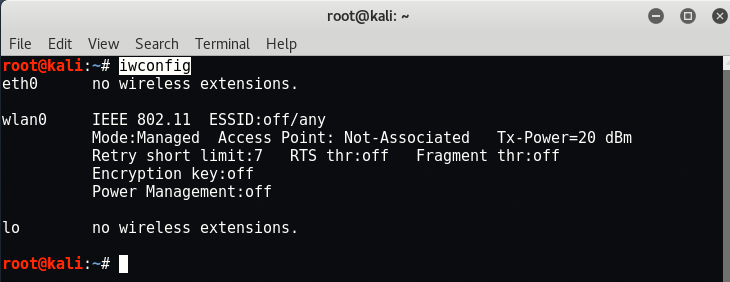
Jak stworzyć masę fałszywych sieci WiFi ? KALI LINUX MDK3 ALFA NETWORK AWUS036ACHM. BEACON FLOODING - YouTube

SYN Flood Denial of Service (DOS) Penetration Testing using Kali Linux | Metasploit Framework - YouTube

Hping3 Demo- Kali Linux - Ping Flood and SYN Flood Attack - DOS and DDOS - Explained - CSE4003 - YouTube
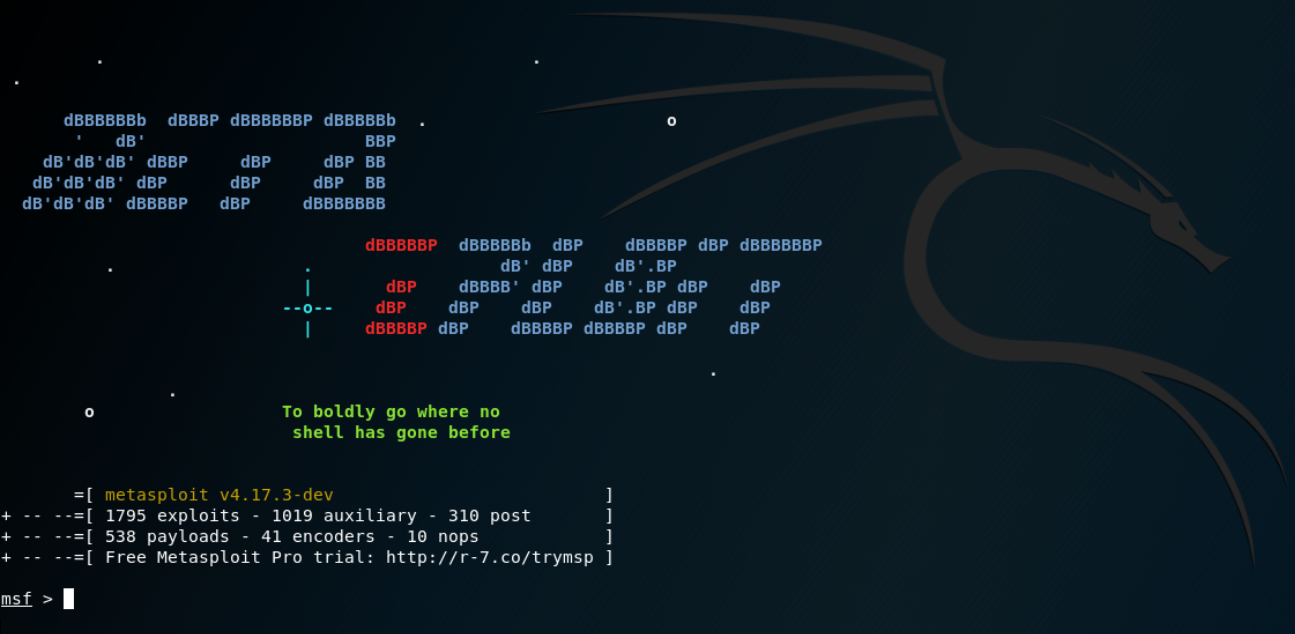

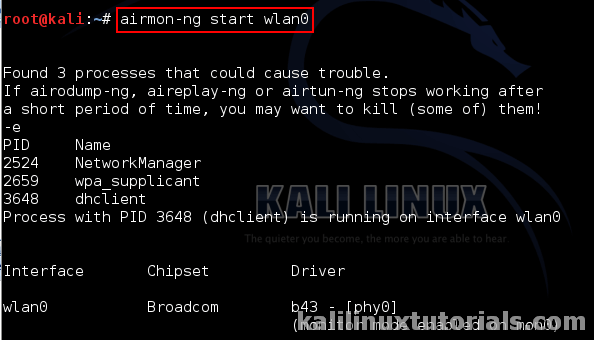

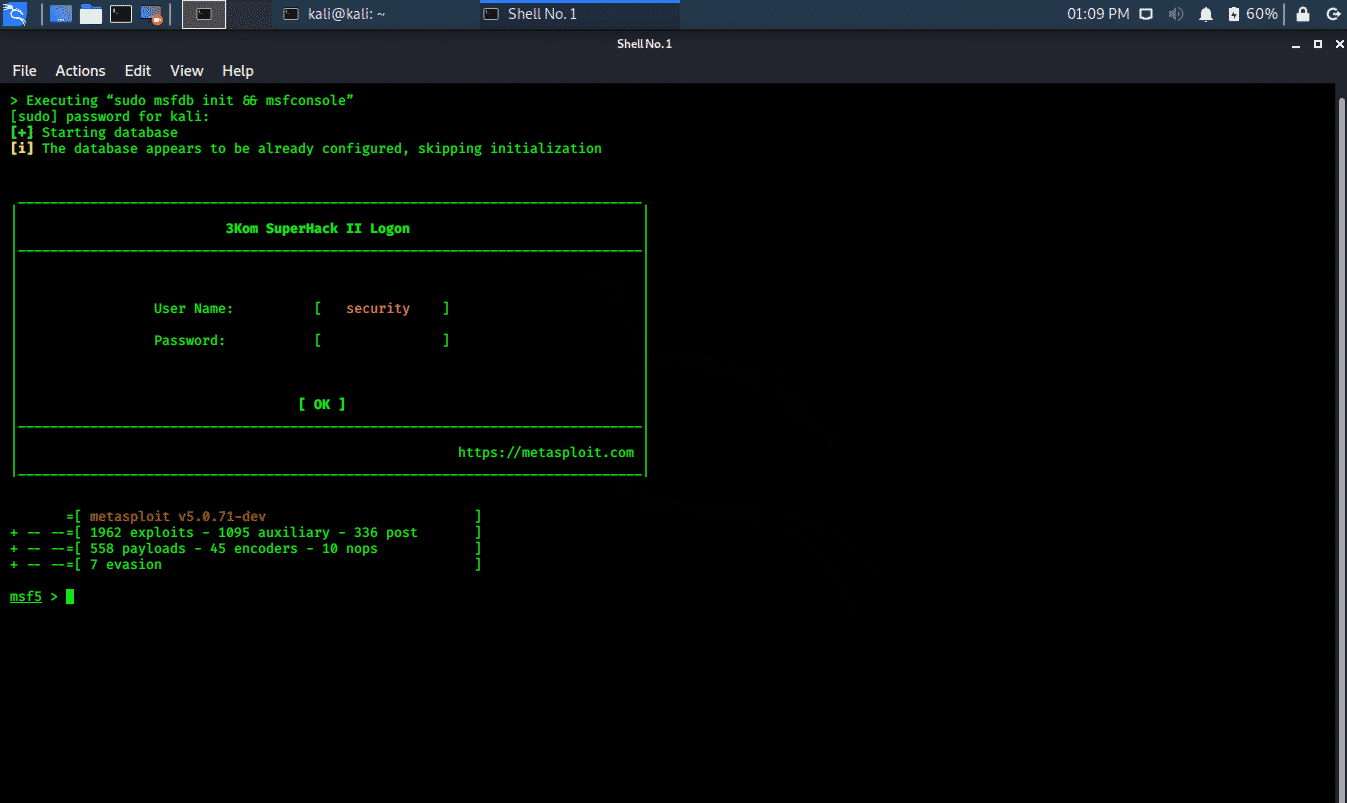
![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/1-177.png)