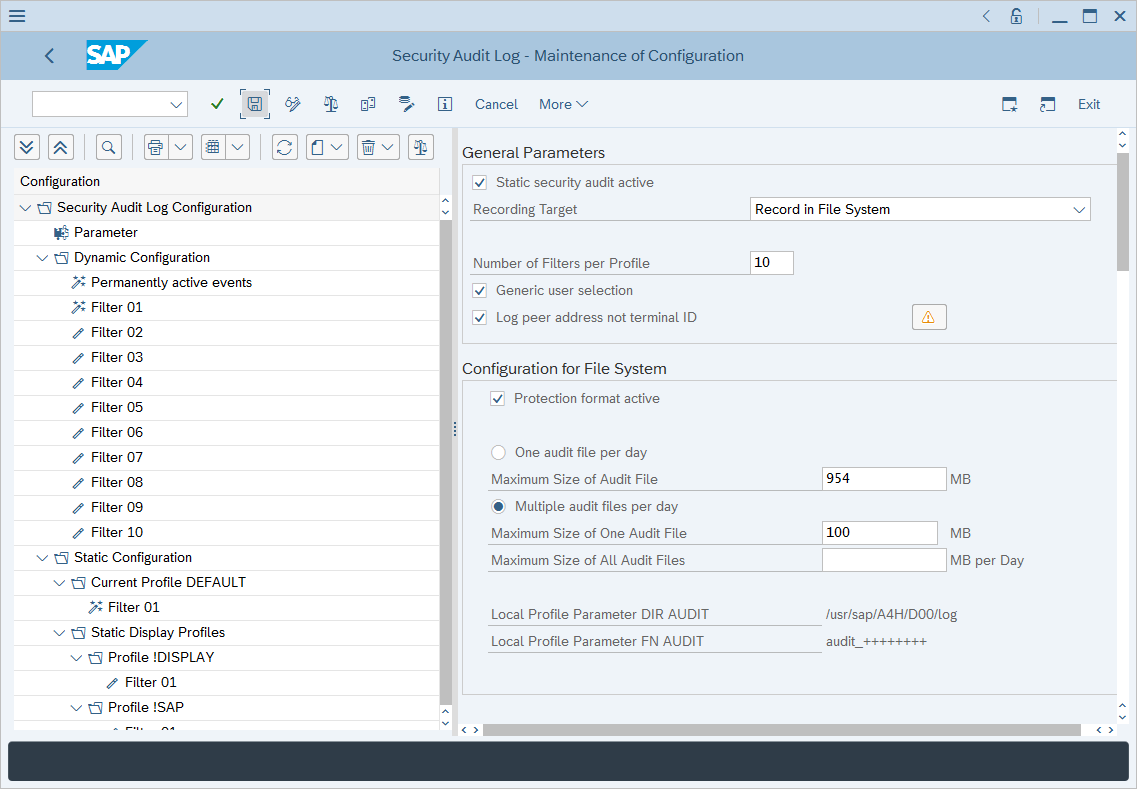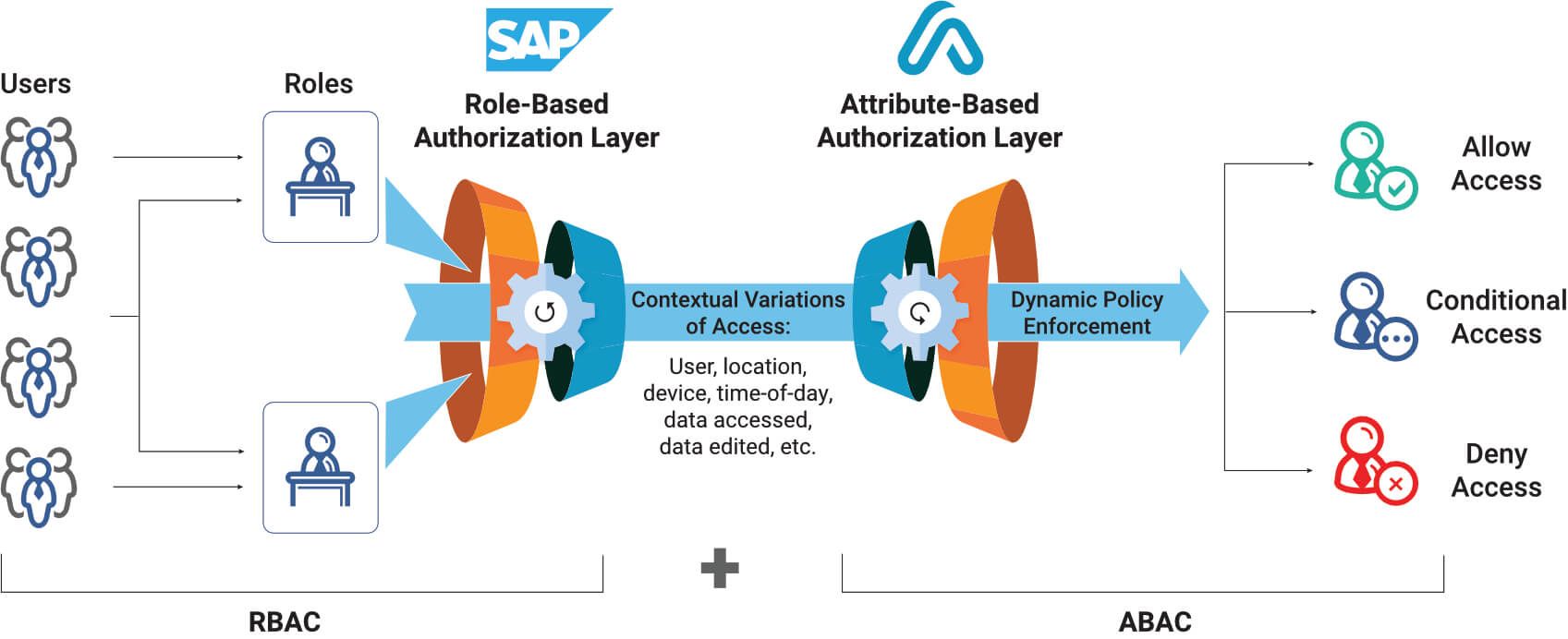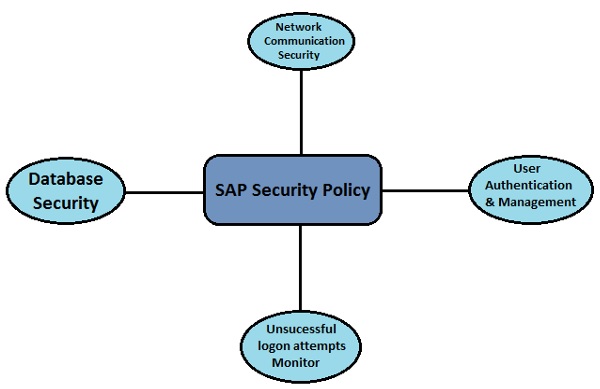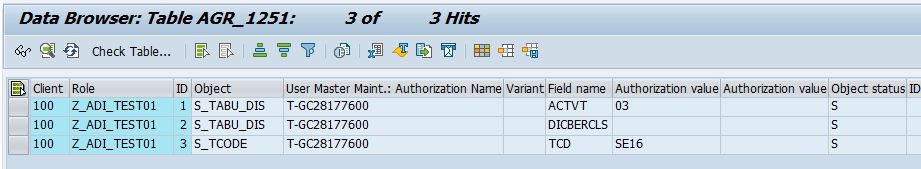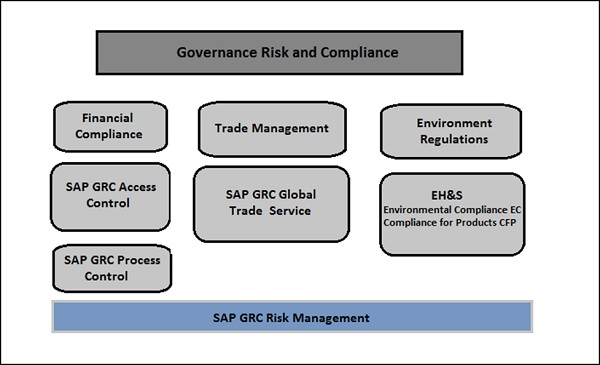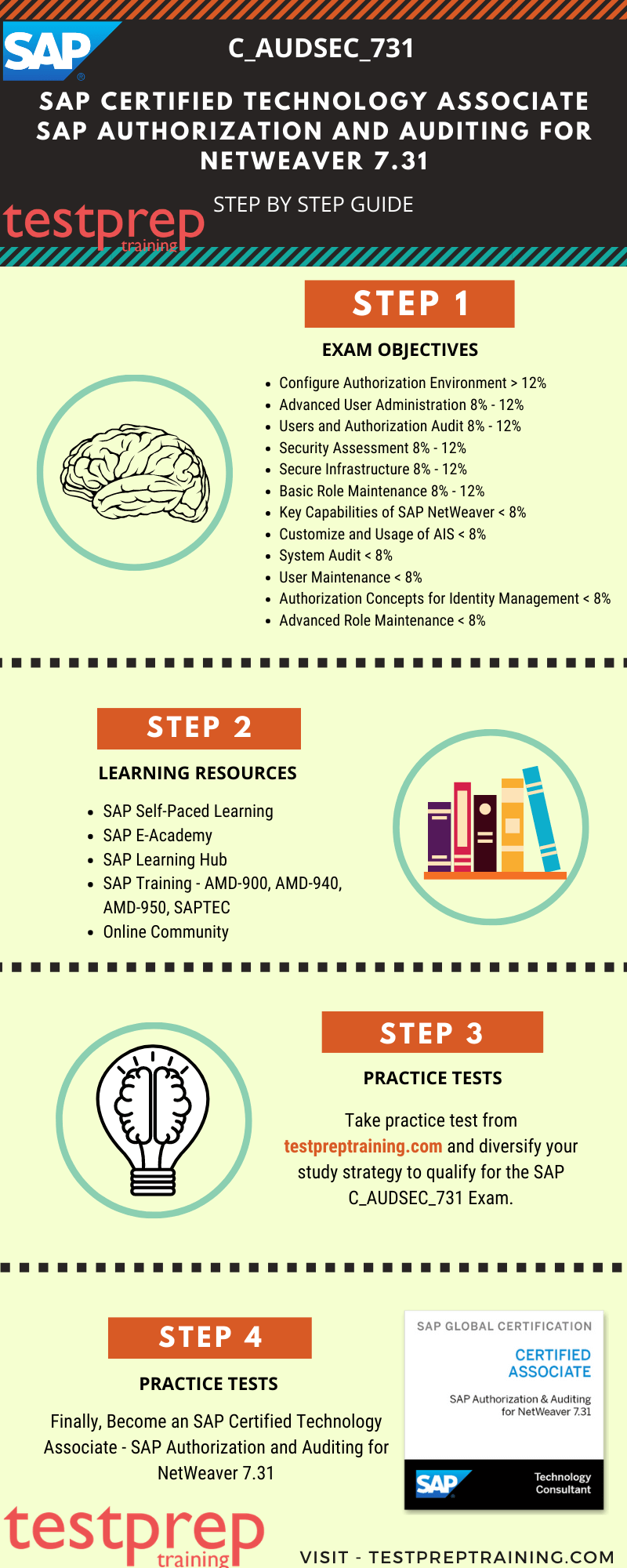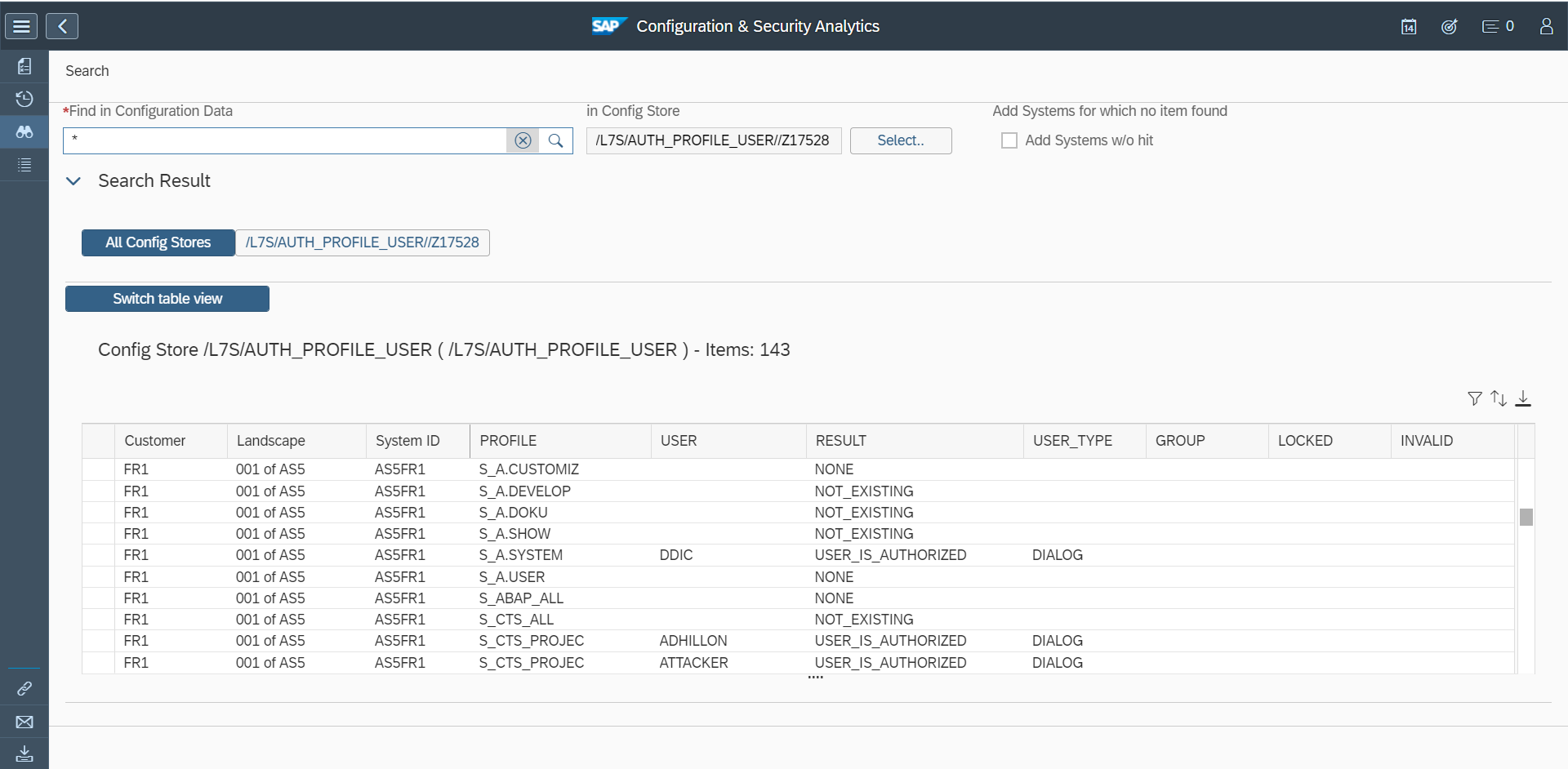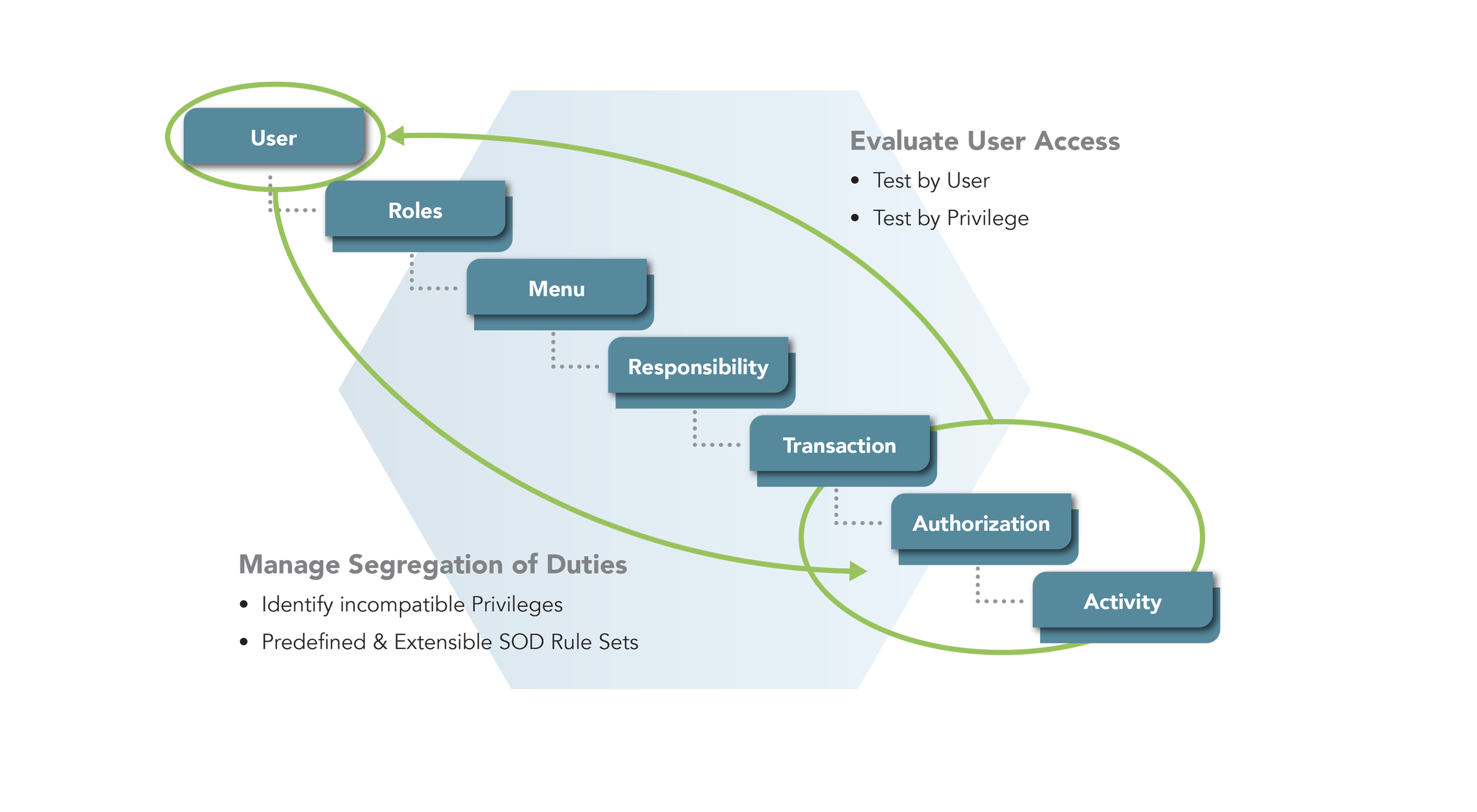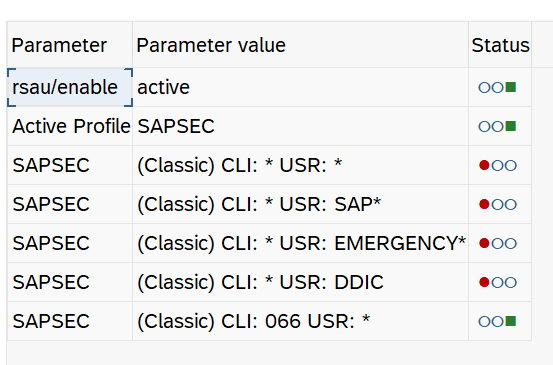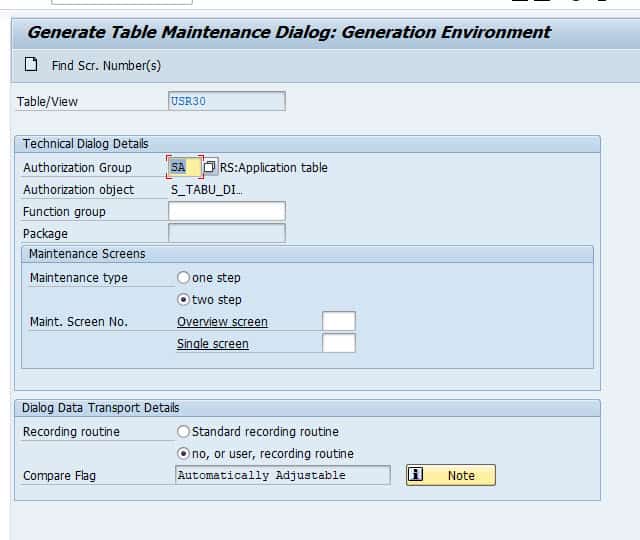
Auditing your SAP Tables for Compliance - ExpressGRC | SAP Cyber Security Software for SAP Compliance

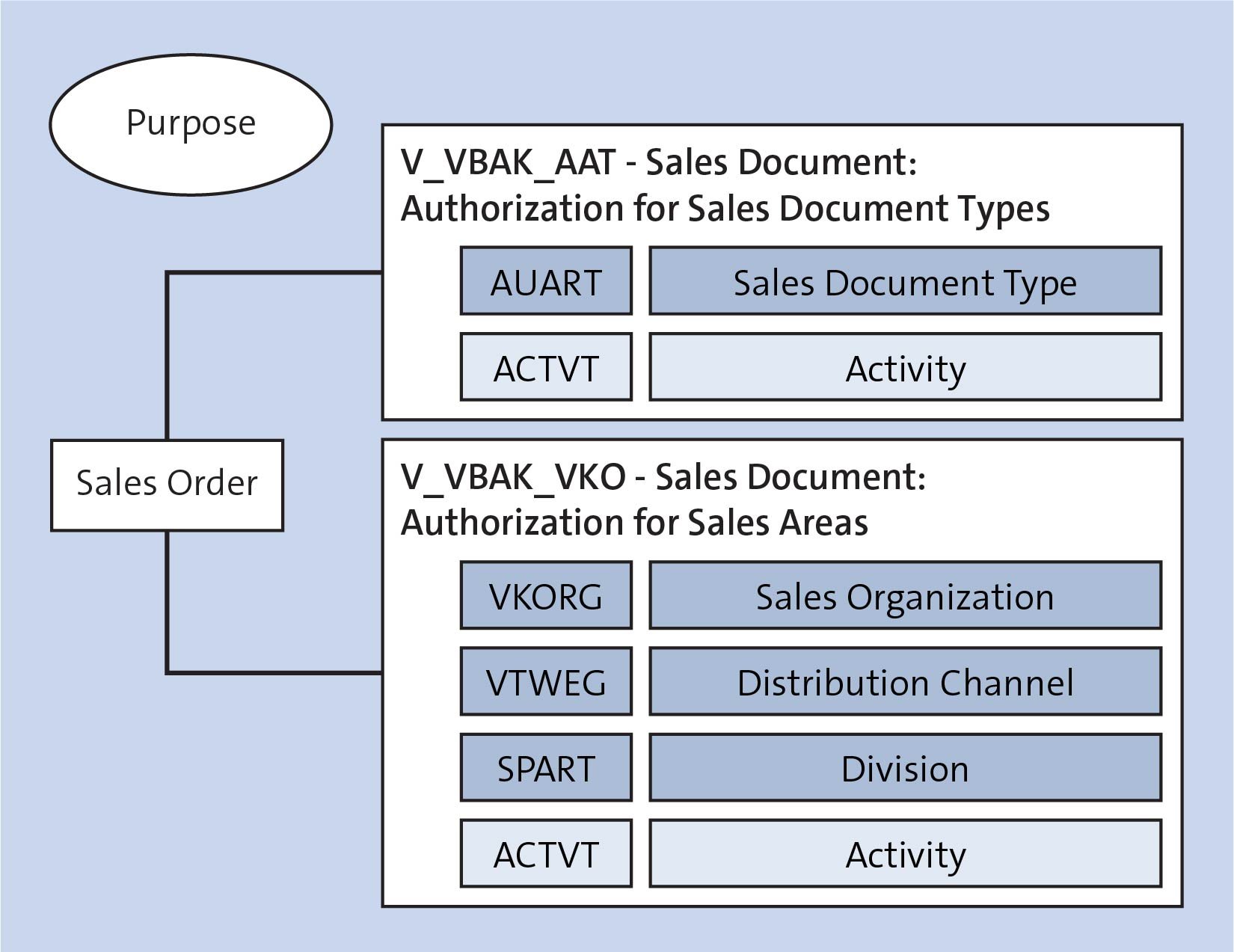
Some Important Information about SAP Authorization Objects as a Functional/Technical Consultant | SAP Blogs
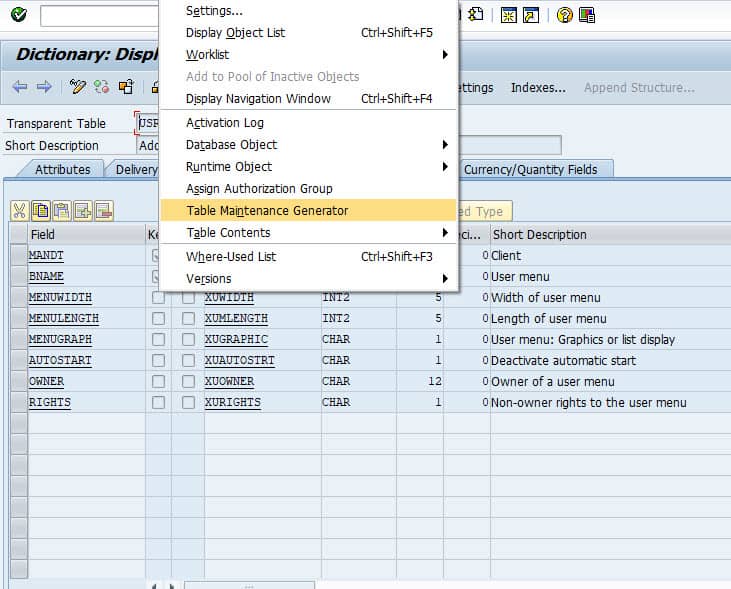
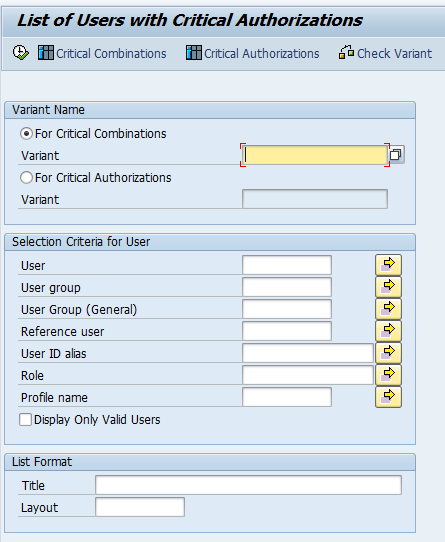
Auditing your SAP Tables for Compliance - ExpressGRC | SAP Cyber Security Software for SAP Compliance